ICS Attacks, The Real National Emergency
News, via the astonishingly prolific security writer Dan Goodin, editing, and reporting at Ars Technica, tells the tale of oil and gas network attacks in the United States, by a group monikered Xenotime. Think we're protected? Think again. Read the Dragos security researcher's post for truly concerning national security relevance.
"The group, now dubbed Xenotime by Dragos, quickly gained international attention in 2017 when researchers from Dragos and the Mandiant division of security firm FireEye independently reported Xenotime had recently triggered a dangerous operational outage at a critical-infrastructure site in the Middle East." via Dan Goodin, Security Editor reporting at Ars Technica
##
"Ultimately, XENOTIME’s expansion to an additional ICS vertical is deeply concerning given this entity’s willingness to undermine fundamental process safety in ICS environments placing lives and environments at great risk. - via Dragos
Buckeye'd
Astounding flaws, reported by both Symantec and Ars Technica... What happended to OpSec? As importantly: The true ramifications for our country are yet unknown... Unless of course, this and other 'leaks' of the same or similar ilk - are, in fact - structured information operations of the highest caliber. Crafted to ensnare the miscreant espionage bounders wandering amongst us... You be the judge.
Key Findings
- The Buckeye attack group was using Equation Group tools to gain persistent access to target organizations at least a year prior to the Shadow Brokers leak.
- Variants of Equation Group tools used by Buckeye appear to be different from those released by Shadow Brokers, potentially indicating that they didn't originate from that leak.
- Buckeye's use of Equation Group tools also involved the exploit of a previously unknown Windows zero-day vulnerability. This zero day was reported by Symantec to Microsoft in September 2018 and patched in March 2019.
- While Buckeye appeared to cease operations in mid-2017, the Equation Group tools it used continued to be used in attacks until late 2018. It is unknown who continued to use the tools. They may have been passed to another group or Buckeye may have continued operating longer than supposed. - via Symantec Corporation's Threat Intelligence Blog
GPS, The Rollover
Failures abound in the GPS realm (due to the recent week rollover on Saturday 2019/04/06). Read Stephen Foskett's superb piece explaining all; and, a presentation on GPS Week Rollover Issues direct from our Government...]. h/t
Bye-Bye, DNA - Hello GSK (and others)
via The Outline's author, Paris Martineau, comes this tale of opt-in/opt-out, GlaxoSmithKline 23andMe. and of course, The Goods - , your DNA. Of which, results in a nagging question: Why would I (or you for that matter), agree to hand over my uniquely identifying DNA data to a commercial enterprise (that only answers to it's shareholders, and only has it's best interests in mind) to use as they see fit? Oh, and a couple of other questions: Do you trust a big-pharma corporation with your own personal Map of Life? What about the future use of that data, once it's in the slipstream of artificially intelligent genetic-testing-reliant health insurance companies? Food for Thought or just Paranoia? You be the judge; after all, it's your DNA, right?
"In short, most — if not all — of the information 23andMe has on its users has probably been shared with someone that isn’t 23andMe itself, and money might have even changed hands. Which is all perfectly within the company’s rights to do, since they agreed to it (probably blindly) when they signed up." - via The Outline author Paris Martineau in the well crafted post 'How To Sign Away The Rights To Your DNA'
Hardware Envelope, A Secure Conveyance →
via Samuel H. Moore, writing at the IEEE's Spectrum Magazine, comes word of the 'Unhackable Envelope'. The Fraunhofer team (developers of the Unhackable Envelope) comprised of Vincent Immler - Fraunhofer Institute for Applied and Integrated Security (AISEC), Martin König - Fraunhofer Research Institution for Microsystems and Solid State Technologies (EMFT), Johannes Obermaier - Fraunhofer Institute for Applied and Integrated Security (AISEC), Matthias Hiller - Fraunhofer Institute for Applied and Integrated Security (AISEC) and Georg Sigl - Fraunhofer Institute for Applied and Integrated Security (AISEC) & Technical University of Munich (TUM) appeared at the IEEE International Symposium on Hardware Oriented Security and Trust in Washington, D.C. last week. Additionally, the group's paper 'B-TREPID: Batteryless Tamper-Resistant Envelope with a PUF and Integrity Detection' won the 2018 Best Paper Award at the confrenece (Kudo's are certainly in order!).
Healthcare Systems - Ransomware Targets →
Superb accounting of the built-to-fail systems in healthcare, and the predeliction of those same systems towards victimization by ransomware attacks. Via Robert N. Charette writing at the IEEE's Spectrum Magazine.
Clouding Up →
via Gizmodo investigative reporter Dell Cameron, comes the astounding news of the systemic incompetence in properly handling secret documents and other artifiacts stored within the cloud (in this case, AWS S3 Buckets) by a well established contractor to the National Geospatial-Intelligence Agency (NGA). Certainly, a first-rate example of an Expanding Cloud of Lethal Stupidity (ECOLS).
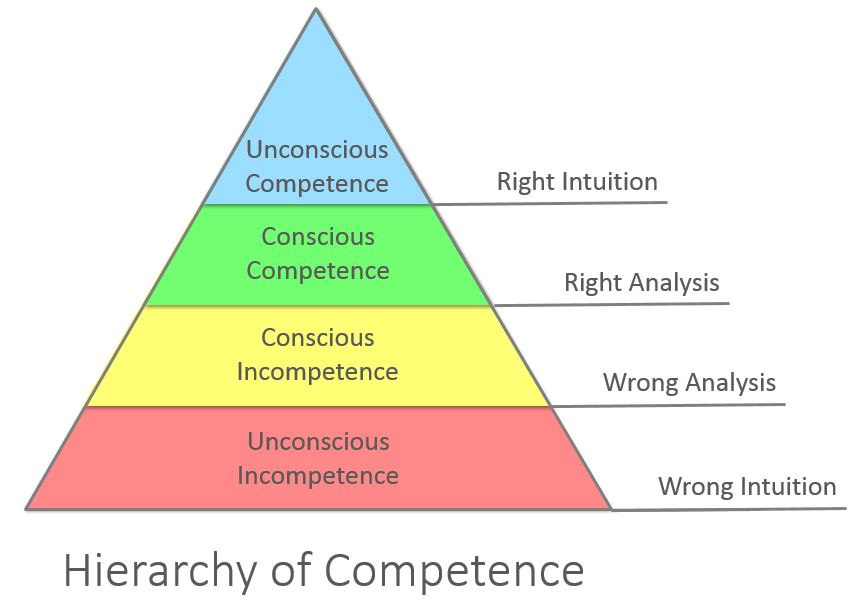
Where does the organization in question fall within the Noel Burch Hierarchy of Competence model?. Should the culprits in this scenario be prosecuted? You be the judge. Truly astounding, indeed.
"A cache of more than 60,000 files was discovered last week on a publicly accessible Amazon server, including passwords to a US government system containing sensitive information, and the security credentials of a lead senior engineer at Booz Allen Hamilton, one of the nation’s top intelligence and defense contractors. What’s more, the roughly 28GB of data contained at least a half dozen unencrypted passwords belonging to government contractors with Top Secret Facility Clearance." - via Gizmodo reporter Dell Cameron
Deutsche Telekom, Drone Hunter →
Apparently, Deutsche Telekom is now in the anti-drone business, utilizing a partner toolkit - monikered 'DroneTracker', and branded - interestingly - the 'Magenta Drone Protection Shield'...
'DroneTracker, developed by Dedrone in Kassel, is the key system that detects drones automatically by means of various sensors – such as video cameras, radio frequency scanners, and microphones – and repels them if necessary. At its core is smart software that is able to distinguish drones from birds, helicopters, and other flying objects safely, and even to recognize specific drone models.' - via HelpNet Security
XKCD, Backups →
via Randall Munroe at XKCD. Enjoy.