Clouding Up →
via Gizmodo investigative reporter Dell Cameron, comes the astounding news of the systemic incompetence in properly handling secret documents and other artifiacts stored within the cloud (in this case, AWS S3 Buckets) by a well established contractor to the National Geospatial-Intelligence Agency (NGA). Certainly, a first-rate example of an Expanding Cloud of Lethal Stupidity (ECOLS).
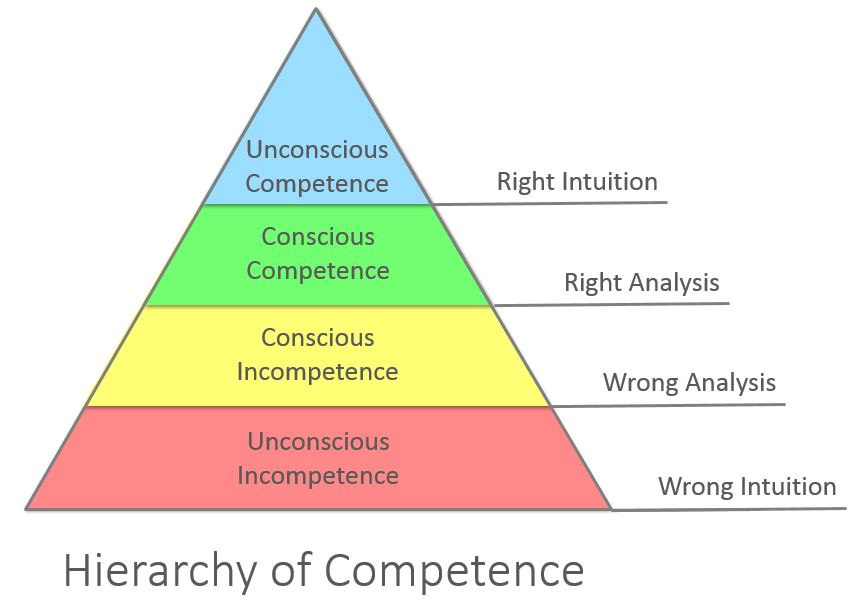
Where does the organization in question fall within the Noel Burch Hierarchy of Competence model?. Should the culprits in this scenario be prosecuted? You be the judge. Truly astounding, indeed.
"A cache of more than 60,000 files was discovered last week on a publicly accessible Amazon server, including passwords to a US government system containing sensitive information, and the security credentials of a lead senior engineer at Booz Allen Hamilton, one of the nation’s top intelligence and defense contractors. What’s more, the roughly 28GB of data contained at least a half dozen unencrypted passwords belonging to government contractors with Top Secret Facility Clearance." - via Gizmodo reporter Dell Cameron
Whom Done It →
In what wraps up to be a superbly crafted screed penned by Glenn Greenwald, laboring at The Intercept; in which, the Good Mr. Greewald details the perceived falsehoods swirling about the alleged Russian Intelligence Services hacks of the Burlington Vermont electrical generation utility. Today's Must Read.
Julian's Grounded
Ecuador's moves imply an effort to protect relations with the United States of America, in their termination of Assanges' internet access, citing attempts to influence elections. Certainly a prudent choice.
Reportage →
The House Permanent Select Committee on Intelligence has voted in the affirmative to adopt the investigative report on Edward Snowden... While the full report is classified as SECRET, the unclassified executive summary is not. Read it and Weep.
Forbidden Research - Snowden's MIT →
Anti-espionage bombast? Nothing more than diatribe-like vaporware? You be the judge...
"Unauthorized Code" In Juniper Firewalls, The Decryption Litany →
via the inimitable Dan Goodin and writing at Ars Technica, wherein the good Mr. Goodin, in a display of remarkable restraint, tells the tale of the discovery of code (in this case not 'authorized') making itself at home in Juniper network componentry. In this case, firewall network componentry. Ooops
Snowden Annointed, Europe Bends The Knee →
Apparently the European Union has nearly canonized Edward Snowden (in a non-binding piece of legislation). That is, of course, if the EU Parliament could annoint sainthood on a living person. Astounding.
Espionage, The Intelligence Files
News, via Lucian Constantin, writing at PCWorld, details the discovery of a targeted group of LinkedIn Corporation (NasdaqGS: LNKD) users (in this case information security professionals) unwittingly involved in a focused intelligence/espionage campaign to garner discrete corporate information. Another case of social networks as the baseline method for intelligence gathering by nations-states and illicit non-governmental organizations. Aye me buckos! A treasure-trove thee awaits!
FireEye Exposed Years-Long APT Attack →
In astonishing (yet unsurprising) news - a discovery by FireEye Labs (and published under the company's Threat Research blog) - of a decade-long espionage campaign by miscreants thereto (in thi case, allegation point to entities in the Peoples Republic of China). FireEye has announced the availability of an indicators download on GitHub here; the full report is available here. Clear proof of why security professionals should be quite concerned, specifically those folks who rely on *deeply flawed and nearly useless enterprise anti-virus and anti-malware products employed throughout most, if not all, enterprise IT environments... Ladies and Gentlemen, Girls and Boys, behold the money quote:
"All of the key findings we examined in the report lead us to conclude that APT 30 is a professional, cohesive threat group with a long-term mission to steal data that would benefit a government, and has been successful at doing so for quite some time. Such a sustained, planned development effort coupled with the group’s regional targets and mission, suggest that this activity is state sponsored." - via FireEye Labs and the FireEye Threat Research blog
Equation Group →
Going dark in 2014, the Equation Group's malware command and control servers have reportedly been migrated onto United States soil... This, after a nefariously successful run targeting thousands of victims in at least 40 countries. Focusing on vertical industry segments such as medical, telecom and aerospace sectors, including diplomatic missions, research institutions, military, governments, the Equation Groups' malware is apaprently fostering speculation as to connections between and betwixt US agencies.
"In an exhaustive report published Monday at the Kaspersky Security Analyst Summit here, researchers stopped short of saying Equation Group was the handiwork of the NSA—but they provided detailed evidence that strongly implicates the US spy agency." - via ArsTechnica's Dan Goodin
Turing's Bletchley Notes Discovered
In an astonishing turn of luck, Alan Turing's Banbury Notes have turned up as roof insulation, at Beltchley Park's Hut 6. Reportedly, the notes were discovered during the renovation of the Hut in 2013.
iOS Espionage Tool Discovered
In a typically fascinating post, over at TrendLabs, written by Lambert Sun, Brooks Hong (Mobile Threat Analysts) and Feike Hacquebord (Senior Threat Researcher), we learn of a recently discovered iOS espionage tool. Ladies and Gentlemen, Girls and Boys, behold, the money quote:
"We found two malicious iOS applications in Operation Pawn Storm. One is called XAgent (detected as IOS_XAGENT.A) and the other one uses the name of a legitimate iOS game, MadCap (detected as IOS_ XAGENT.B). After analysis, we concluded that both are applications related to SEDNIT. The obvious goal of the SEDNIT-related spyware is to steal personal data, record audio, make screenshots, and send them to a remote command-and-control (C&C) server. As of this publishing, the C&C server contacted by the iOS malware is live." - via TrendMicro's TrendLabs blog authors Lambert Sun, Brooks Hong and Feike Hacquebord.
Bureau Releases Additional Evidence of DPRK Complicity
Ah, news outlets are reporting evidence release by the United States Department of Justice's Federal Bureau of Investigation; in this case detailing DPRK complicit activity in the now infamous SONY hack...